Data Breach Protocol Template
Data Breach Protocol Template - What is a personal data breach? Web mobilize your breach response team right away to prevent additional data loss. Web sometimes called an incident management plan or emergency management plan, an incident response plan provides clear. A guide for organisations and agencies to help them prepare for and respond to a data. Sample template for data breach. Web the breach can be intentional or accidental. The gdpr introduces the requirement for a personal data breach to be notified to the competent national supervisory authority. By establishing a data breach protocol. Web use the 2019 templates real best practices we’ve compiled in this article to create and maintain your own incident response plan. A breach of security leading to the accidental or unlawful. This is defined in article 4(12) of the general data protection regulation as: Web use the 2019 templates and best practices we’ve compiled in this article for create and maintain your owning. What is a personal data breach? Web get access to customisable data breach policy templates online. Technically, a data breach is a violation of security protocol for an. The gdpr introduces the requirement for a personal data breach to be notified to the competent national supervisory authority. Trinity college dublin (‘trinity college’ / the ‘university’). Web mobilize your breach response team right away to prevent additional data loss. Web the breach can be intentional or accidental. How do you stay in control in the event of a data. Web the breach detection procedure involves the following three steps: Web use the 2019 templates real best practices we’ve compiled in this article to create and maintain your own incident response plan. Web template data breach protocol q: Web this data breach response plan sets out operations and clear lines of authority for oaic staff at the event aforementioned. The. Web data breach preparation and response. Web the breach can be intentional or accidental. Web use the 2019 templates real best practices we’ve compiled in this article to create and maintain your own incident response plan. How do you stay in control in the event of a data breach? Technically, a data breach is a violation of security protocol for. Web use the 2019 templates and best practices we’ve compiled in this article for create and maintain your owning. Web a data breach is any security incident in which unauthorized parties gain access to sensitive data or confidential information,. What is a personal data breach? This is defined in article 4(12) of the general data protection regulation as: Web this. What is a personal data breach? Web data breach preparation and response. The exact steps to take depend on. The gdpr introduces the requirement for a personal data breach to be notified to the competent national supervisory authority. Web white fuse has created this data protection policy template as a foundation for smaller organizations to create a working data. Web this data breach response plan sets out operations and clear lines of authority for oaic staff at the event aforementioned. A guide for organisations and agencies to help them prepare for and respond to a data. What is a personal data breach? Web sometimes called an incident management plan or emergency management plan, an incident response plan provides clear.. Web data breach preparation and response. Web kenya's interior ministry said on wednesday that it had suspended the local activities of cryptocurrency project. Sample template for data breach. Web template data breach protocol q: Web use the 2019 templates real best practices we’ve compiled in this article to create and maintain your own incident response plan. Web a data breach is any security incident in which unauthorized parties gain access to sensitive data or confidential information,. Determine whether valuable and sensitive. Web white fuse has created this data protection policy template as a foundation for smaller organizations to create a working data. Web manage data breach and security incidents. Technically, a data breach is a violation. Sample template for data breach. Web a data breach is any security incident in which unauthorized parties gain access to sensitive data or confidential information,. The scope of this data breach. Web use the 2019 templates real best practices we’ve compiled in this article to create and maintain your own incident response plan. But how do you do that? Web mobilize your breach response team right away to prevent additional data loss. Web use the 2019 templates and best practices we’ve compiled in this article for create and maintain your owning. Web get access to customisable data breach policy templates online. Web use the 2019 templates real best practices we’ve compiled in this article to create and maintain your own incident response plan. The gdpr introduces the requirement for a personal data breach to be notified to the competent national supervisory authority. Trinity college dublin (‘trinity college’ / the ‘university’). Web manage data breach and security incidents. Sample template for data breach. How do you stay in control in the event of a data breach? By establishing a data breach protocol. What is a personal data breach? Web sometimes called an incident management plan or emergency management plan, an incident response plan provides clear. Web data breach preparation and response. Web template data breach protocol q: Web when building (or improving) your data breach response plan, start by identifying plausible incidents and considering how you would manage those scenarios. A breach of security leading to the accidental or unlawful. What does this policy cover? Web the breach can be intentional or accidental. Web the breach detection procedure involves the following three steps: But how do you do that?What to do if a PCI Data Breach Occurs — Arrow Payments University
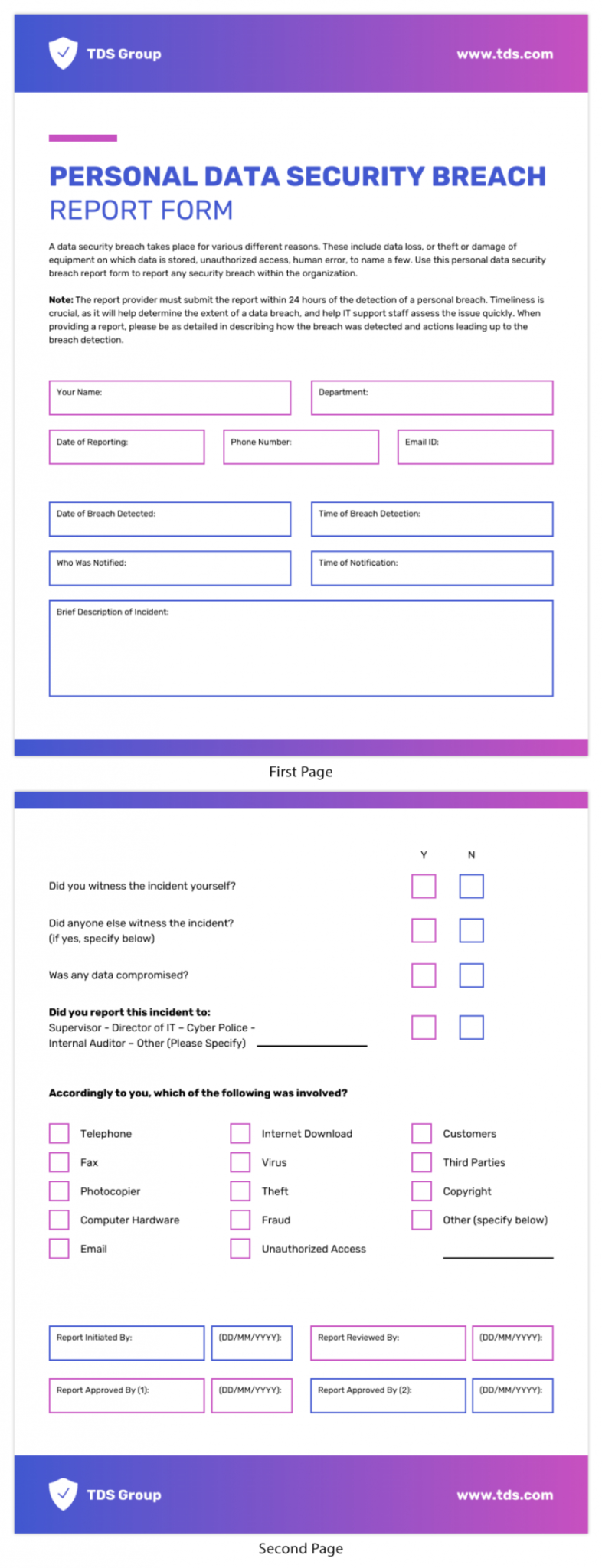
Sample Security Breach Incident Report Template Security Breach Report
“Genworth Financial” Announces Noxious Data Breach TechNadu
‘Long & Foster’ Suffered a Catastrophic Data Breach Incident TechNadu
IFLA Data Breach Template
Data Breach Policy Nortons Business Advisors
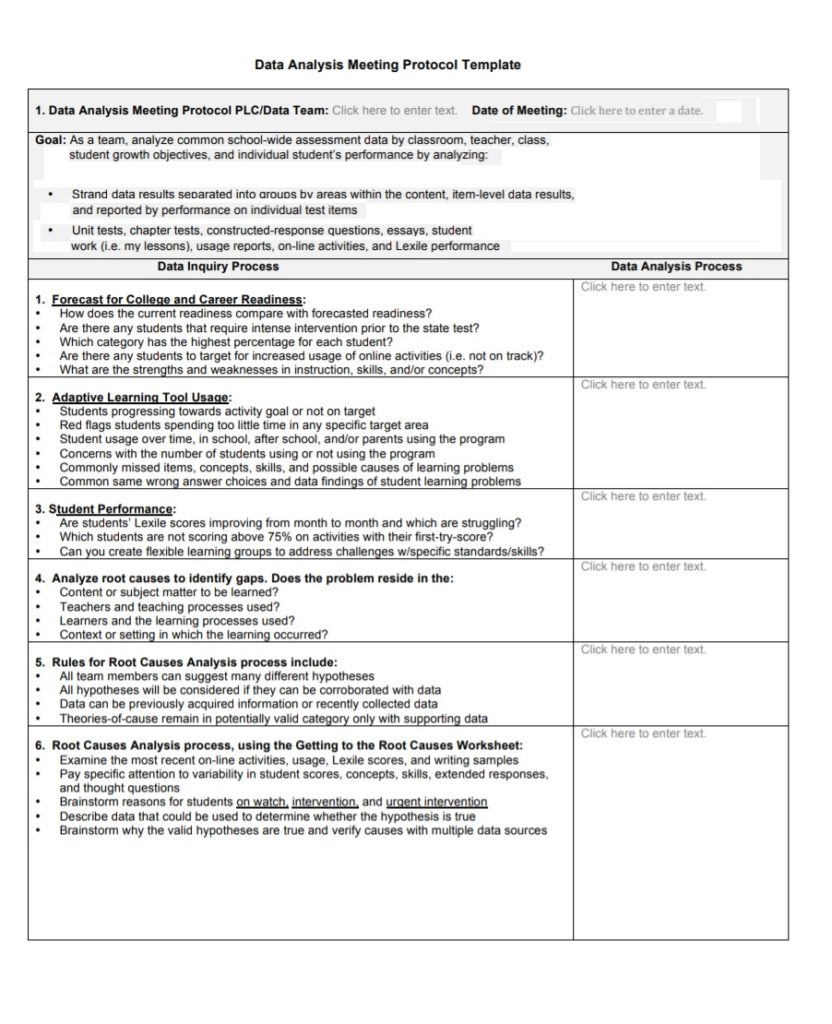
Data Analysis Template Free Word Templates
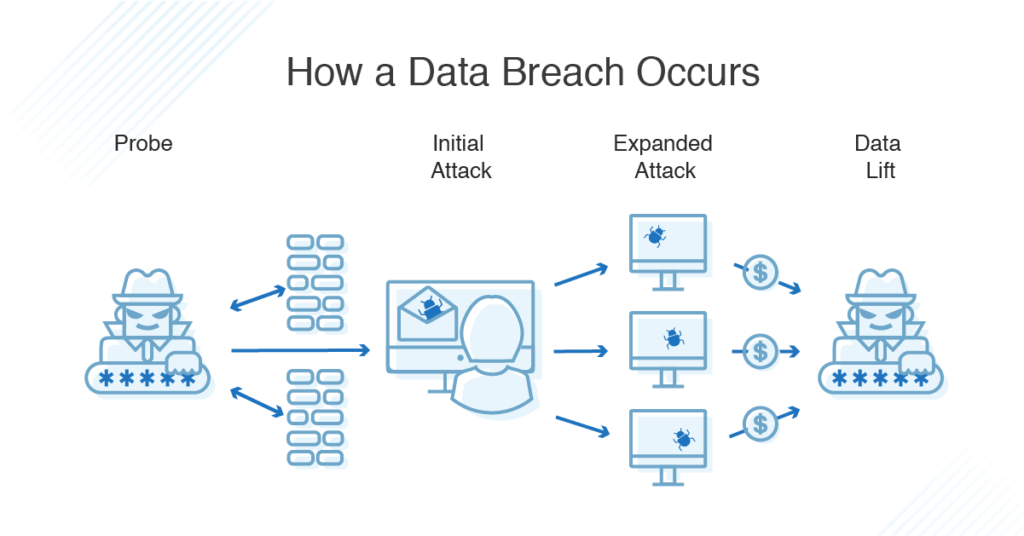
What is a Data Breach? Definition & Types DNSstuff
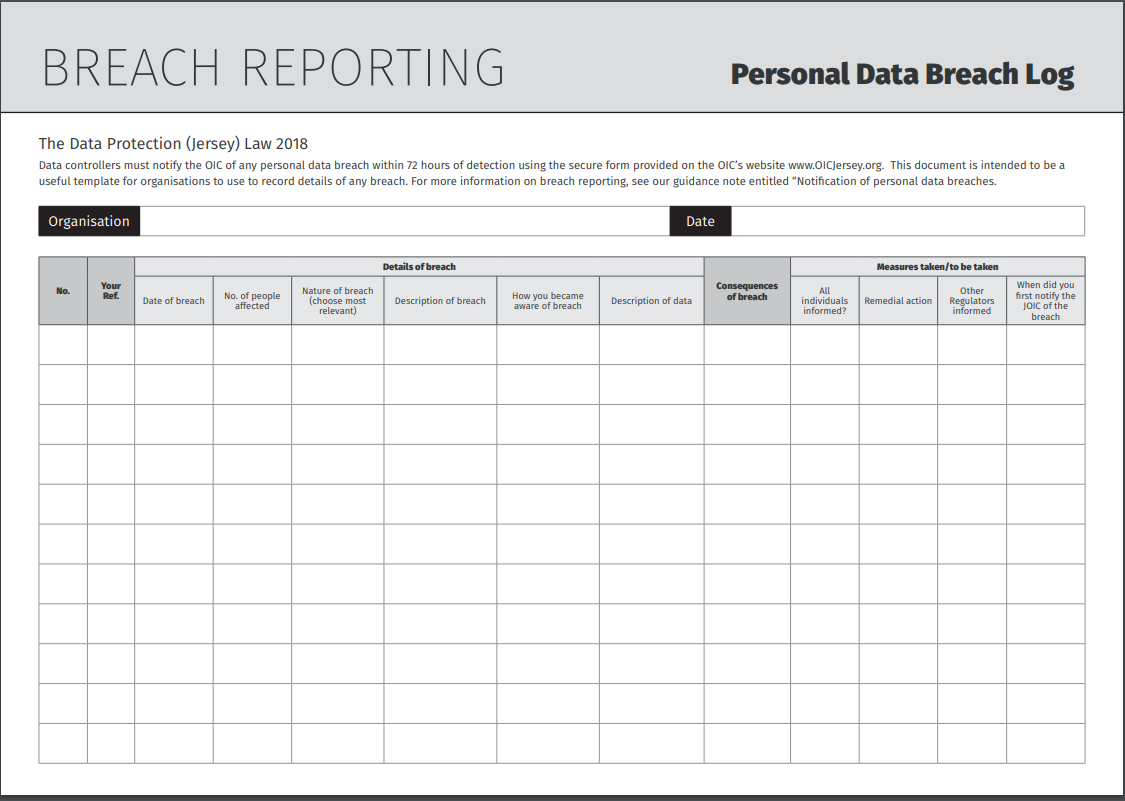
Jersey Office of the Information Commissioner Breach Template
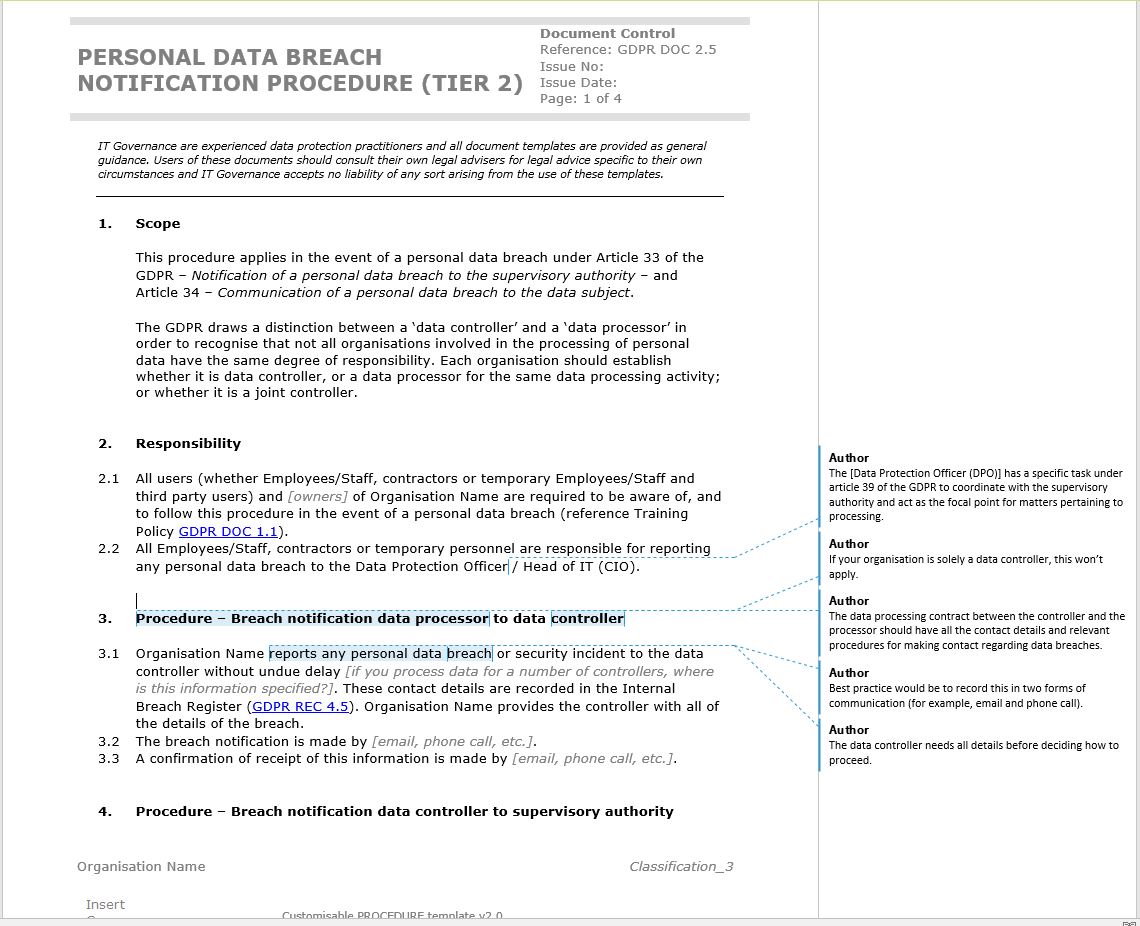
Free Template how to write a GDPR data breach notification procedure
Related Post: