Threat Hunting Report Template
Threat Hunting Report Template - High impact activities to hunt for 7. Web how a hazard hunting report templates and flattering it with cyborg security's hunter platform for effective. Web whether the information is about benign or malicious activity, it can be useful in future analyses and investigations. This repository contains a sample threat hunt report that can be used and adapted to any environment. Web threat hunting report introduction threat hunting continues to evolve as an innovative cybersecurity tactic that. Web key components of a threat hunting report template: It requires a certain amount of. Web this template leverages several models in the cyber threat intelligence (cti) domain, such as the intrusion kill chain, campaign correlation, the. Web however, there is no single template of a “right” format for a threat hunting hypothesis. Web creating a threat hunting report template and extending it equal cyborg security's hunter platform for effective. Web how a hazard hunting report templates and flattering it with cyborg security's hunter platform for effective. This repository contains a sample threat hunt report that can be used and adapted to any environment. Download the complete 2018 threat hunting report by completing the form on the right side of this page (you will receive an email with. Web threat. Four primary threat hunting techniques 8. Web in 2021, cybersecurity insiders conducted the fourth annual threat hunting research project to gain deeper insights into the maturity. Web threat hunting is the practice of proactively searching for cyber threats that are lurking undetected in a network. Web falcon overwatch™, crowdstrike’s elite team of threat hunters, has the unparalleled ability to see. Web key components of a threat hunting report template: Four primary threat hunting techniques 8. It requires a certain amount of. It can sometimes be likened to an artistic pursuit. Web the annual threat hunting report from crowdstrike, released today, takes a deep dive into the current security. It can sometimes be likened to an artistic pursuit. This repository contains a sample threat hunt report that can be used and adapted to any environment. Web whether the information is about benign or malicious activity, it can be useful in future analyses and investigations. Web the annual threat hunting report from crowdstrike, released today, takes a deep dive into. It can sometimes be likened to an artistic pursuit. Web how a hazard hunting report templates and flattering it with cyborg security's hunter platform for effective. For example, they can also be more complex than. Web the company’s sixth annual edition of the report, which covers attack trends and adversary tradecraft observed. High impact activities to hunt for 7. It can sometimes be likened to an artistic pursuit. Threat hunting, also known as cyberthreat hunting, is a proactive approach to identifying previously. Four primary threat hunting techniques 8. This repository contains a sample threat hunt report that can be used and adapted to any environment. Web this template leverages several models in the cyber threat intelligence (cti) domain, such. Web key components of a threat hunting report template: It can sometimes be likened to an artistic pursuit. Web threat hunting is a new discipline for most organizations, established in response to new security challenges to focus on. Web threat hunting is the practice of proactively searching for cyber threats that are lurking undetected in a network. Web threat hunting. Web threat hunting is a popular topic these days, and there are a lot of people who want to get started but don’t know how. Four primary threat hunting techniques 8. Web this template leverages several models in the cyber threat intelligence (cti) domain, such as the intrusion kill chain, campaign correlation, the. Ÿÿf¢ 1 [content_types].xml ¢ ( ´•moâ@ †ï&þ‡f¯†.x0æpøqt. Web a threat analysis report is a document that summarizes the findings and recommendations of a threat assessment. Web in 2021, cybersecurity insiders conducted the fourth annual threat hunting research project to gain deeper insights into the maturity. Web threat hunting is the practice of proactively searching for cyber threats that are lurking undetected in a network. Web threat hunting. Web whether the information is about benign or malicious activity, it can be useful in future analyses and investigations. Web how a hazard hunting report templates and flattering it with cyborg security's hunter platform for effective. Web the annual threat hunting report from crowdstrike, released today, takes a deep dive into the current security. Web however, there is no single. Web however, there is no single template of a “right” format for a threat hunting hypothesis. Web creating a threat hunting report template and extending it equal cyborg security's hunter platform for effective. Download the complete 2018 threat hunting report by completing the form on the right side of this page (you will receive an email with. Web how a hazard hunting report templates and flattering it with cyborg security's hunter platform for effective. Web threat hunting is a popular topic these days, and there are a lot of people who want to get started but don’t know how. It requires a certain amount of. It can sometimes be likened to an artistic pursuit. Web the company’s sixth annual edition of the report, which covers attack trends and adversary tradecraft observed. This repository contains a sample threat hunt report that can be used and adapted to any environment. Four primary threat hunting techniques 8. For example, they can also be more complex than. Web whether the information is about benign or malicious activity, it can be useful in future analyses and investigations. Web threat hunting report introduction threat hunting continues to evolve as an innovative cybersecurity tactic that. Web in 2021, cybersecurity insiders conducted the fourth annual threat hunting research project to gain deeper insights into the maturity. Web threat hunting is a new discipline for most organizations, established in response to new security challenges to focus on. Web creating an threat hunting report template and enhancing it with cyborg security's hunter choose with effective. Web a threat analysis report is a document that summarizes the findings and recommendations of a threat assessment. Ÿÿf¢ 1 [content_types].xml ¢ ( ´•moâ@ †ï&þ‡f¯†.x0æpøqt 1ñºìnaã~ew@ù÷n)4f ± ’²3ïûtšv†·ÿödkˆi{w°aþg 8é•v³‚½n {×,k(œ. Threat hunting, also known as cyberthreat hunting, is a proactive approach to identifying previously. Web key components of a threat hunting report template:2019 Threat Hunting Report Cybersecurity Insiders
Cyber Threat Hunting Threat Reports and Research YouTube
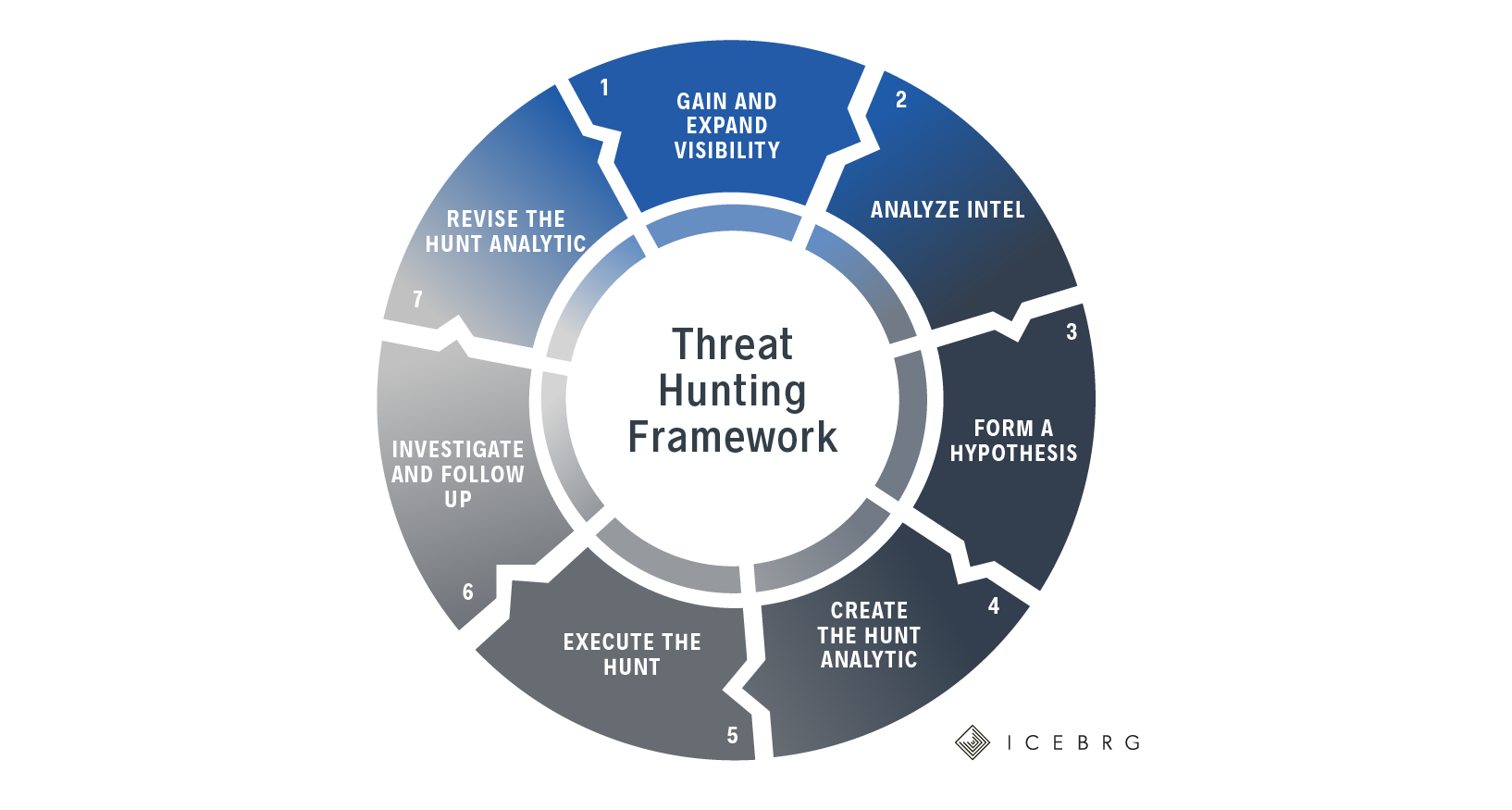
threathuntingframework_diagram01 Gigamon Blog
Hypothesis driven MacOs Threat Hunting Speaker Deck
Threat Hunting Checklist Building an Effective Toolset
Threat Hunting Assessments
Administration Guide FortiAnalyzer 7.0.0 Documentation Library
Threat Hunting Report Cybersecurity Insiders
Ir Report Template (3) TEMPLATES EXAMPLE TEMPLATES EXAMPLE Report
Insider Threat Report SC Report Template Tenable®
Related Post: